PHD RESEARCH TOPIC IN INFORMATION SECURITY
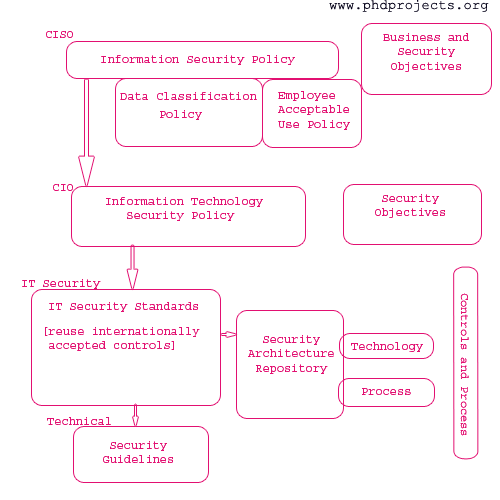
PHD RESEARCH TOPIC IN INFORMATION SECURITY is an interesting area for research due to its omnipresent usage. Millions of people use internet and store personnel information. Each day thousands of transaction takes place online. During all such process, information needs to be validated and stored secure. It has evolved a new field namely Information security. Information security is a set of business process that protects information assets regarding how the information is formatted or it is processed or being stored. So It is best practise to prevent the unauthorized access, inspection, recording, or destruction.
Information-Security
Most prevalent PHD RESEARCH TOPIC IN INFORMATION SECURITY is Information security and privacy health care: adoption of digital patient records, increased regulation, provider consolidation and increasing need for information exchanged between the patients, providers, and to all payers lead to the need of security. It is also used in HW implementation security, applied cryptography, cryptograptanalysis fields by providing non-linear error detection for finite state machines.
Evaluation of quadratic equations from a kind of s-boxes is another important application. Researcher can choose information security for the betterment of society. It will give them astounding opportunity to prove themselves due to its real time operation. Also, It can be best implemented as a product with our support. We have preeminent developers and coders who can implement most complex projects with minimum time duration.
RESEARCH ISSUES IN INFORMATION-SECURITY:
Forensic based also on analysis
Attack prevention also in system
Intrusion detection also in system
Key cryptographic technologies
Authentication also in system
Privacy based also on protection
Security
Access control based also on mechanisms
Identity based also on management
Trusted based also on computing
Mobile security search
Financial management also in system
Mobile security etc.
SOFTWARE AND TOOL DETAILS
=============================
1)TBsecure
2)Jasypt
3)CrypTool
4)PKWare
5)scrypt
6)Wireshark
7)OWASP – ZAP
8)DIGIPASS
PURPOSE OF THE EVERY SOFTWARE AND TOOL
===========================================
TBsecure–> Standard C secure coding also used to identify issues like buffer overflow, out-of-bounds array access, dangling pointers etc
Jasypt–>Provides also basic encryption capabilities
CrypTool–> e-learning tool also which illustrates cryptographic and cryptanalytic concepts.
PKWare–> Provides embedded encryption and also performance options.
scrypt–>Used also to encrypt passwords.
Wireshark–> performs packet also analysis of network traffic
OWASP – ZAP–> Works also for web application security
DIGIPASS–> comprehensive software development kit (SDK) which integrates application security, Two-factor authentication and also electronic signing into mobile applications.
Save
Related Search Terms
Information security research issues, Information security research topics, phd projects in Information security, Research issues in Information security
FAQ
1.What are the tools used for information security based projects?
Tools like TBsecure, Jasypt, CrypTool, PKware, OWASP, DIGIPASS etc are few tools which we can use for information security based projects. We can implement in any tool which you will bring to us as learning a new tool is just two days work for us.
2.Do you implement BYO method?
BYO indicates bring your own method. We will always support such concepts as we always provide different solution to same problem.
3.What algorithms can be used for phishing problem?
Many security algorithms can be used but it depends upon the project need. We will can guide you better, if you approach us with complete detail.
Tools
- TBsecure
- Jasypt
- CrypTool
- PKWare
- scrypt
- Wireshark
- OWASP - ZAP
- DIGIPASS